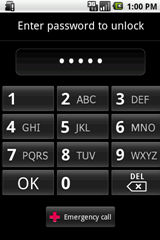
 Another day, another Android security vulnerability. Ars Technica reports on the latest one, whereby an Android device with a password-based lockscreen can be unlocked by opening the camera and entering a long string of characters into the password field.
Another day, another Android security vulnerability. Ars Technica reports on the latest one, whereby an Android device with a password-based lockscreen can be unlocked by opening the camera and entering a long string of characters into the password field.
Google released a patch for its own Nexus Android devices, but not everyone has a Nexus, and not even all of the Nexus devices have received the patch yet. And as we all know, non-Google Android devices often update much more slowly. Meanwhile, PIN- or pattern-based lockscreens aren’t vulnerable to this particular glitch, so if you’re worried about it, you might want to change your lock mode.
It seems like news of new vulnerabilities comes out every couple of weeks, but just consider how complicated modern computer devices are, and how many different systems and subsystems that make them up. As many different parts as go together to make them up, it’s something of a miracle that they’re even as secure as they are.































